If you are using WordPress for your business or blog, it’s really important to do a WordPress Security Audit security of your WordPress website. In WordPress plugins, vulnerability is considered as the main reasons for the attacks Exploiting a vulnerability in the outdated and unsecured third party plugin is always the best target for the attackers. WordPress is the most popular CMS platform suffers more than 55% of attacks, due to the plugin vulnerability issues.
Simply, an attacker can establish a connection between a vulnerable plugin and make a connection between your website and perform his action.
Always not just the faulty plugin of WordPress is responsible, sometimes extensions, modules are creating a different kind of security issues. Mostly for the bigger cyber attacks plugin developer comes into the high pressure. They have to work around the clock to patch that security treat ASAP.
So now you have an idea that plugin development is not an easy task. There are multiple security measures that theme and plugins developers must have to know. So one such important security measure is to test your plugin for vulnerabilities while developing it. For this, you can start a plugin security audit.
Contents
What is WordPress Plugin Security audit VAPT
Vulnerability Assessment and Penetration testing is the types of vulnerability test. VAPT is the combination of tests that gives you the best reports about your plugin development security.
Vulnerability assessment, as from the name you can guess that in this test you can find out the different vulnerability present, and on the other hand in penetration testing will find the ways to exploit those vulnerabilities. These tests will help us to determine how much damage it can cause to the website. The VAPT assessment gives a report about the existing plugin vulnerabilities and the potential way to exploit them, and how much damage a website will bear if in case the attacker hacks into the website.
The developer consists of proper knowledge and the tools can conduct the security audits. Vulnerability assessments and penetration tests are mostly done by ethical hackers, they are also known as White Hat hackers. Who will exploit your vulnerable ports and gives you knowledge about the exploitable software like a plugin.
That being said at the end of this tutorial you will have enough knowledge to conduct successful plugins security audits.
Before starting the guide you must have to know about the most common plugins security vulnerabilities that can affect your Website and you must have to do WordPress Security Audit.
Common WordPress Security Vulnerability
Cross-site scripting (XSS)
Arbitrary file viewing
Arbitrary file upload
Privilege escalation
SQL injection
Remote code execution (RCE)
Cross-site request forgery (CSRF)
How to perform a WordPress security audit for Plugin (developers perspective)
WordPress security audit for plugin consists of three steps Reconnaissance (i.e. Information gathering), Exploitation, and Remediation.
WordPress Security Audit for a plugin varies from developers and their purposes Different plugins have different purposes for the audits. Almost every WordPress plugins need to check these things.
- Testing all input areas on the plugin
- Checking requests made by the plugin
- Checking the source code
- Checking permissions and data storage on the plugin
1. Gathering Information
The first test of every vulnerability assessment is to start with Information gathering about your plugin. This information shall help you in prioritizing the security areas in your plugin that you need to test first.
Commonly checked security areas in your that are tested in every plugin are user input, and related checks (validation, escaping), files & directories permissions, configurations, data storage, encryption, web servers, database, and more.
To perform this kind of task there are some automated tools to make your work easy, and helps you to find security issues in each of these security areas. Tools like Nikto, Nmap, Testssl, etc can help you to fast forward the process of vulnerability assessment.
Nikto
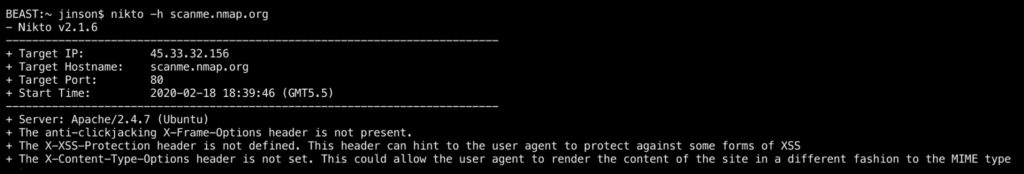
Nikto is a Kali Linux based pentest tool. Which is popular for finding out the information like server, hostname, port, IP, security headers, etc. of an application.
To perform the task by Nikto, you need to run the following command.
# nikto –h [yourwebsiteurl]where yourwebsiteurl is your server IP or FQDN.
Nmap
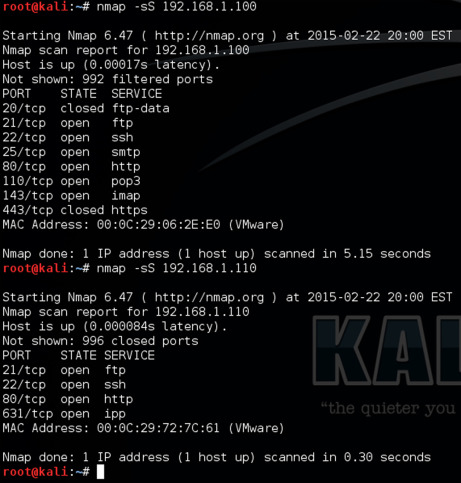
Nmap stands for network mapper, this one is also a very popular pen-testing tool used to perform network pretesting, monitoring the host & server uptime. In simple words, Nmap gives you information about the hosting for that particular web application. That includes the name of the hosting service, Version, Operating systems, and firewalls or security system if they have, Nmap tells you about all.
Just type in the following command to run Nmap in Kali Linux
nmap -sV -Pn [examplewebserverurl]
2. Exploitation
By this time you have an idea that which kind of vulnerabilities are present in WordPress plugins. Now the next step is to exploit the vulnerabilities present in the plugin. This will help you to learn how easily each vulnerability can be exploited and the level of damage it can cause to your WordPress websites.
There are tool available to perform this kind of tests such as SQLmap, Burp Suite.
SQLmap
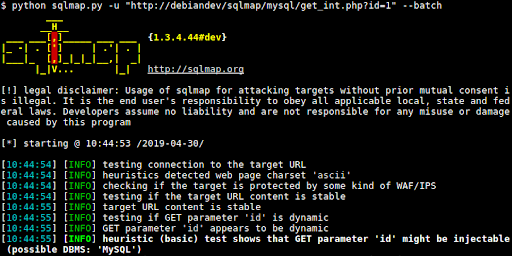
SQLmap is the tool developed to exploit the vulnerabilities related to the database. This tool is basically used to crack open the database by executing malicious queries into the plugin’s input fields.
To run this tool in your kali linux system you need to run the following command.
sqlmap -u “yourwebsite.com?scan=test” –dbs
Burp Suite

Burp Suite consists of multiple pen-testing tools. Burp Suite can be used in any stage of the WordPress plugin security audit. The tool caters to both – security assessment and vulnerability exploitation. The tools included in Burp Suite is HTTP Proxy, Scanner, Intruder, Spider, Repeater, Decoder, Comparer, Extender & Sequencer.
Alright, you are now equipped with adequate information about vulnerabilities, now you can easily resolve the WordPress plugin vulnerability.
Final words
Just a single WordPress plugin vulnerability it can totally ruin your website. Because of the plugin vulnerability, thousands of new and old websites are affected daily. Some of them are recovered and some are not and eventually they shut down, to save you and your plugin from this kind of situation you need to do a detailed plugin security audit or plugin security assessment. A plugin VAPT helps you to find and rectify security flaws in your WordPress plugin.
Also Read: Best Free Software Uninstallers in 2020
(Related Searches: WordPress Security Audit, WordPress Security Audit for plugin, WordPress plugin Security Audit, Tools for WordPress Security Audit)